Buffer overflow Essays Video
Writing a Simple Buffer Overflow Exploit Buffer overflow EssaysIntroduction Invalidated inputs are always a big threat to website security.
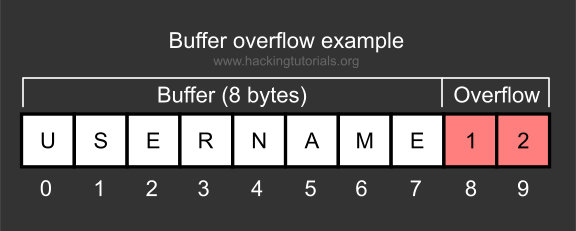
In this activity, you will discuss the popular buffer overflow attack and its countermeasures. The hacker bypasses the authentication and logs into the software.
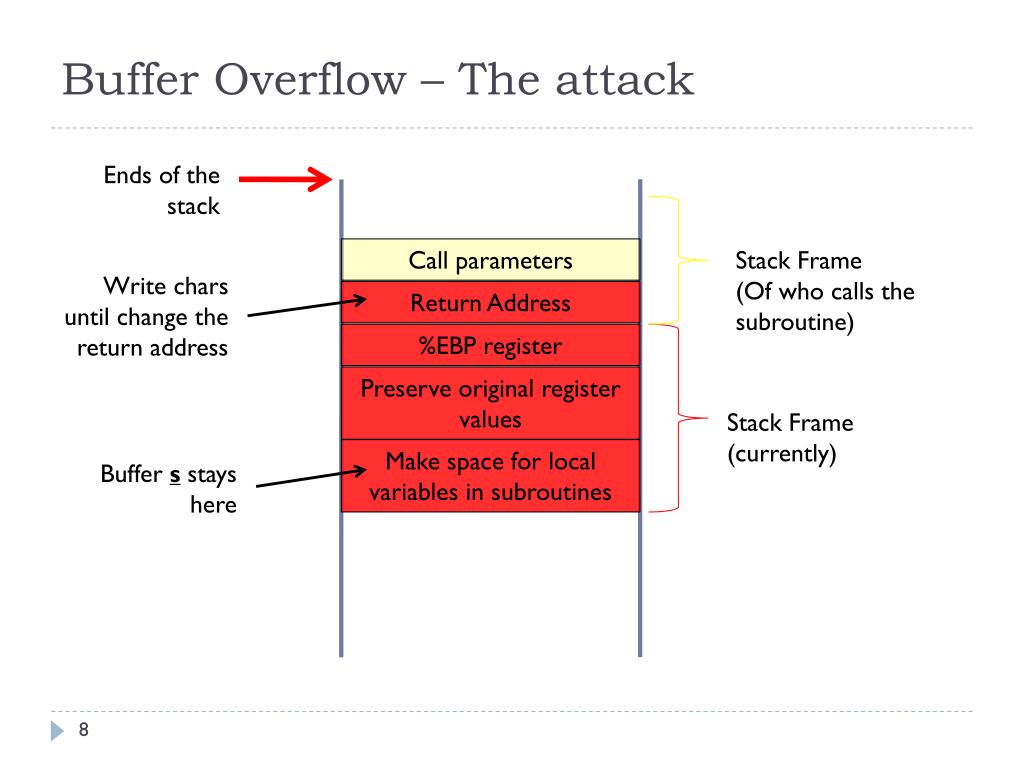
Analyze the following program to identify the possible cause of Buffee breach in the code. Explain how hackers inject shellcodes into the system using a Buffer Overflow Attack. After posting your initial response, select two of your peers to discuss how you would each refine the code to mitigate the vulnerabilities in the existing code. Get Expert Help at an Amazing Discount!]

Rather useful piece
I congratulate, your opinion is useful
I know a site with answers to a theme interesting you.
Curiously, but it is not clear